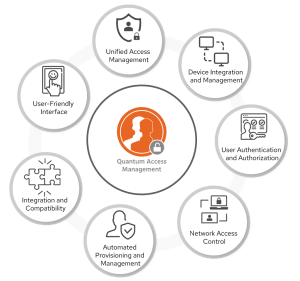
Managing access to networks, applications and devices is a critical aspect of organizational security and efficiency. With the proliferation of various endpoints and the rise of remote work, the task of ensuring seamless yet secure access has become increasingly complex. This is where Quantum Access Manager (QAM) steps in, offering a comprehensive and unified solution to streamline access control processes. Let’s see how QAM does all of these.
Unified Access Management:
At its core, QAM is designed to simplify access control by providing a single platform to manage access across a wide array of resources. Whether it’s enterprise devices, guest users, BYOD scenarios or IoT devices, QAM offers a unified approach to access management, reducing complexity for IT administrators
Device Integration and Management:
QAM allows seamless integration of enterprise-provided devices into your network. From laptops to smartphones, it ensures these devices work harmoniously within your infrastructure while maintaining security and consistency. Additionally, QAM extends its support to IoT devices, allowing organizations to connect and control smart devices without sacrificing security or efficiency.
User Authentication and Authorization:
Security is paramount in access management and QAM provides robust measures to ensure that only authorized personnel can access resources. Features like Single Sign-On (SSO) and Two-Factor Authentication (2FA) bolster security measures while enhancing the user experience by simplifying login processes.
Network Access Control:
Controlling access to networks, whether wireless or wired, is essential for maintaining network security. QAM empowers administrators to define access policies, ensuring only authorized individuals can connect to these networks. This enhances network security and provides administrators with greater visibility and control over network access.
Automated Provisioning and Management:
Managing access rights for users and devices can be a challenging task, especially in large organizations. QAM simplifies this process through automated provisioning, ensuring that the right individuals have the necessary permissions without manual intervention. This not only saves time but also reduces the risk of human error in access management.
Integration and Compatibility:
QAM seamlessly integrates with various identity management tools, such as Ping and Okta, enhancing compatibility with existing infrastructure. It also supports multiple authentication and authorization sources, including Active Directory and LDAP, providing organizations with flexibility in their access control strategies.
User-Friendly Interface:
Ease of use is paramount in any IT solution and QAM delivers with an intuitive interface and dashboards. Administrators can easily navigate through various features and settings, making access management a hassle-free experience.
Today, when data security and access management are paramount, Quantum Access Manager emerges as a comprehensive solution to streamline access control processes. By offering unified access management, robust security measures and seamless integration, QAM empowers organizations to efficiently manage access to their networks, applications and devices, ultimately enhancing security, productivity and the user experience.